Researchers have discovered a new and powerful transient execution attack called ‘Inception’ that can leak privileged secrets and data using unprivileged processes on all AMD Zen CPUs, including the latest models.
Transient execution attacks exploit a feature present on all modern processors named speculative execution, which dramatically increases the performance of CPUs by guessing what will be executed next before a slower operation if completed.
If the guess is correct, the CPU has increased performance by not waiting for an operation to finish, and if it guessed wrong, it simply rolls back the change and continues the operation using the new outcome.
The problem with speculative execution is that it can leave traces that attackers can observe or analyze to retrieve valuable data that should be otherwise protected.
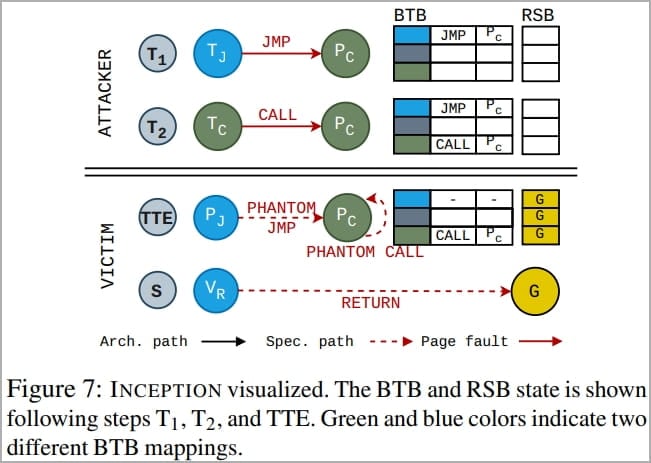
Researchers at ETH Zurich have now combined an older technique named ‘Phantom speculation’ (CVE-2022-23825) with a new transient execution attack called ‘Training in Transient Execution’ (TTE) to create an even more powerful ‘Inception’ attack.
Phantom speculation allows attackers to trigger mispredictions without needing any branch at the misprediction source, i.e., create a speculative execution period (“transient window”) at arbitrary XOR instructions.
TTE is the manipulation of future mispredictions by injecting new predictions into the branch predictor to create exploitable speculative executions.
The Inception attack, tracked as CVE-2023-20569, is a novel attack that combines the concepts described above, allowing an attacker to make the CPU believe that an XOR instruction (simple binary operation) is a recursive call instruction.
This causes it to overflow the return stack buffer with a target address controlled by the attacker, allowing them to leak arbitrary data from unprivileged processes running on any AMD Zen CPU.
The leak is possible even if all mitigations to known speculative execution attacks like Spectre or transient control-flow hijacks, such as Automatic IBRS, have already been applied.
Also, the data leak rate achieved through Inception is 39 bytes/sec, which would take about half a second to steal a 16-character password and 6.5 seconds for an RSA key.
ETH Zurich’s team published separate technical papers for Inception and Phantom for those who want to dive deeper into the specifics of the attacks.
[embedded content]
Preventing Inception attacks
The researchers say that all AMD Zen-based Ryzen and EPYC CPUs, from Zen 1 to Zen 4, are vulnerable to Phantom and Inception.
Specific TTE variants potentially impact Intel CPUs, but Phantom is hard to exploit on Intel thanks to eIBRS mitigations.
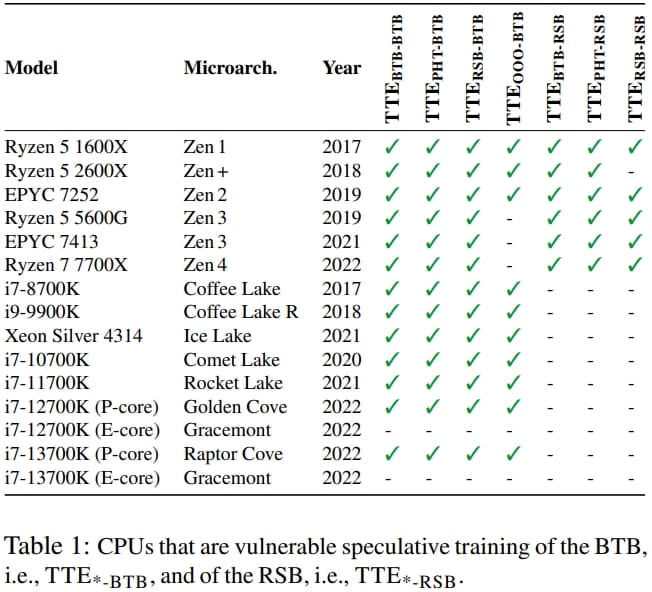
Although the proof-of-concept created by the ETH Zurich team is meant to be executed on Linux, the attacks should work on any operating system using vulnerable AMD CPUs, as this is a hardware flaw, not a software one.
A strategy to mitigate the problem would be to fully flush the branch predictor state when switching between distrusting contexts; however, this introduces a performance overhead between 93.1% and 216.9% on older Zen 1(+) and Zen 2 CPUs.
For Zen 3 and Zen 4 CPUs, adequate hardware support for this mitigation strategy was initially absent, but AMD has since released microcode updates to enable this feature.
Owners of Zen-based AMD processors are recommended to install the latest microcode updates, which can also arrive as part of computer vendor and/or operating system security updates.
A fix for the Phantom flaw, CVE-2022-23825, was released in the Windows July 2022 update.
BleepingComputer has contacted AMD to learn more about microcode release schedules for the impacted chip architectures, but we have yet to hear back by publication time.